This Post Covers error during IDCS Group Lookup Reconciliation Scheduled Jobs, as a part of Oracle Identity Manager (OIM)/Oracle Identity Governance (OIG), Integration with Oracle Identity Cloud Service (IDCS).
Note: Oracle Identity Manager (OIM) has been changed and rebranded as Oracle Identity Governance (OIG).
Error: IAM-1020021 Unable to execute job : IDCS Group Lookup Reconciliation org.identityconnectors.framework.common.exceptions.InvalidCredentialException: HTTP 401 Error : User not authorized to execute service.
Before moving into the Issue & its fix, Lets first understand the Overview of Oracle Identity Cloud Service, IDCS Connector Bundle, Connector server and Scheduled Job.
What is Oracle Identity Cloud Service (IDCS)
Oracle Identity Cloud Service (IDCS) is that provides identity management, single-sign-on (SSO) and identity governance for on-premise or Cloud Applications.
Any user can access the application anytime, anywhere on a device securely. Oracle IDCS integrates directly with existing directories and identity management system, making it easier for users to access applications. Providing a platform that is robust and secure, allows users to access, develop and deploy their applications.
For more details on Oracle Identity Cloud Serve ice (IDCS) Overview & Concepts Click here
What is OIM IDCS Connector Bundle
An Oracle Identity Manager (OIM) connector Bundle is a piece of code that runs on OIM/OIG and Connector Server and used to automatically and continuously provision and reconcile users and groups from OIM/OIG to target system Oracle Identity Cloud Service (IDCS).
What is Connector Server
An Identity connector server is required when an identity connector bundle is not directly executed within your OIM/OIG application. By using one or more identity connector servers, the Identity Connector Framework (ICF) architecture permits your application to communicate with externally deployed identity connector bundles.
There are two Identity connector servers are available
- Java Connector Server
- Microsoft .NET Connector Server
For More details on Connector Server for OIM connectors: .NET or JAVA Click here
Scheduled Job for IDCS Connector
Scheduled jobs for lookup field synchronization fetch the most recent values from specific fields in the target system (IDCS) to lookup definitions in OIM/OIG.
The following scheduled jobs are used for lookup fields synchronization:
- IDCS Groups Lookup Reconciliation
- IDCS Managers Lookup Reconciliation
Issue:
Oracle Identity Manager (OIM) was integrated with Identity Cloud Service (IDCS) using the OIM IDCS connector.
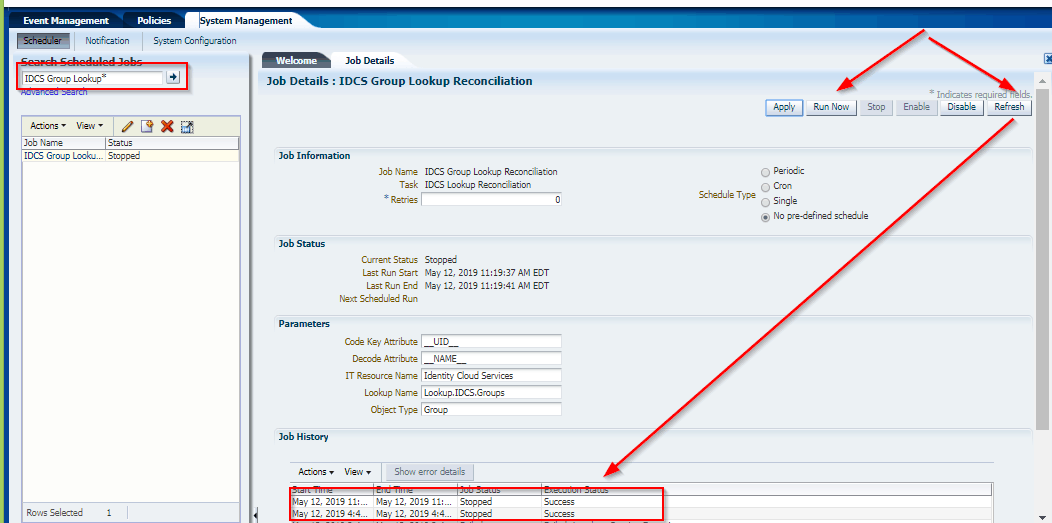
Running schedule job IDCS Group Lookup Reconciliation fails with:
————————————————–
[2019-05-08T05:27:09.923-04:00] [oim_server1] [TRACE] [] [oracle.iam.scheduler.vo] [tid: OIMQuartzScheduler_Worker-8] [userId: oiminternal] [ecid: 0000MdsWf3nFW7WFLzyGOA1Smi79000003,1:26731] [APP: oim#11.1.2.0.0] [SRC_CLASS: oracle.iam.scheduler.vo.TaskSupport$1] [SRC_METHOD: processWithoutResult] Exception encountered
[2019-05-08T05:27:09.923-04:00] [oim_server1] [WARNING] [] [oracle.iam.scheduler.vo] [tid: OIMQuartzScheduler_Worker-8] [userId: oiminternal] [ecid: 0000MdsWf3nFW7WFLzyGOA1Smi79000003,1:26731] [APP: oim#11.1.2.0.0] IAM-1020021 Unable to execute job : IDCS Group Lookup Reconciliation with Job History Id:8061[[
org.identityconnectors.framework.common.exceptions.InvalidCredentialException: HTTP 401 Error : User not authorized to execute service.<HTML><HEAD><META HTTP-EQUIV=”Content-Type” CONTENT=”text/html;charset=UTF-8″><TITLE>Unauthorized</TITLE></HEAD>
<BODY><H1>Unauthorized</H1>
Proper authorization is required for this area. Either your browser does not perform authorization, or your authorization has failed.
</BODY></HTML>
at org.identityconnectors.framework.impl.serializer.CommonObjectHandlers$9.createException(CommonObjectHandlers.java:227)
at org.identityconnectors.framework.impl.serializer.CommonObjectHandlers$9.createException(CommonObjectHandlers.java:224)
at org.identityconnectors.framework.impl.serializer.CommonObjectHandlers$ThrowableHandler.deserialize(CommonObjectHandlers.java:115)
at org.identityconnectors.framework.impl.serializer.binary.BinaryObjectDecoder$InternalDecoder.readObject(BinaryObjectDecoder.java:162)
at org.identityconnectors.framework.impl.serializer.binary.BinaryObjectDecoder.readObject(BinaryObjectDecoder.java:313)
Root Cause:
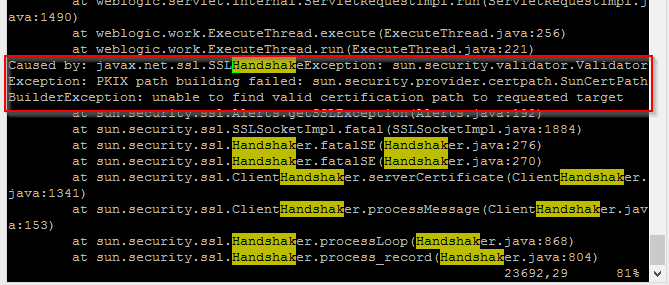
The issue is generic and can have multiple reasons like:
- SSL Handshake fatal Error with IDCS
- Several misconfigurations in the IDCS IT resources in OIM
- Wrong values in the Client application in IDCS
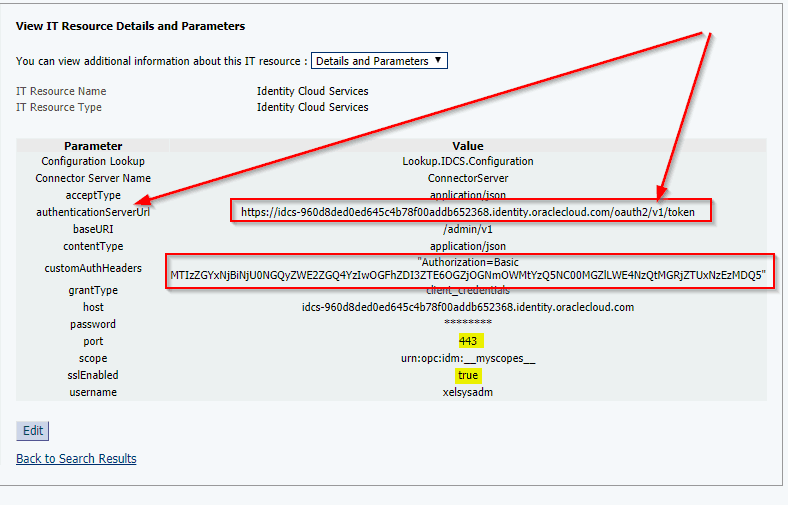
Missconfiguration found at Client case while Configuring IT Resource Parameter
- In Client case, IT Resource Parameter of IDCS Connector authenticationServerUrl was “https://<IDCS Hostname>/oauth2/token” Instead of “https://<IDCS Hostname>/oauth2/v1/token”/v1 was missing in the Oracle documentaion.
- customAuthHeaders in the IT resource in the field We provided this value with the format: Authorization=Basic XXXXXXXXXXXXXXXXXX instead “Authorization=Basic XXXXXXXXXXXXXXXXXX” (double quotes “” was missing between value)
Troubleshooting:
- Check 1: “authenticationServerUrl” should be”https://<IDCS Hostname>/oauth2/v1/token”
- Check 2: The value of field customAuthHeaders needs to be enclosed between double quotes. For Example: “Authorization=Basic MTIzZGYxNjBiNjU0NGQyZWE2ZGQ4Y”
- Check 3: Port number at which the target system (IDCS) is listening.
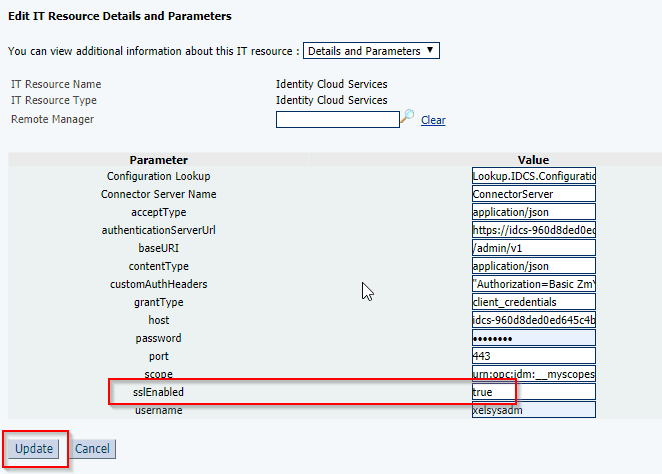
- Check 4: IDCS always expects SSL communication, so sslEnabled must be set on “true” in the IDCS IT Resource.
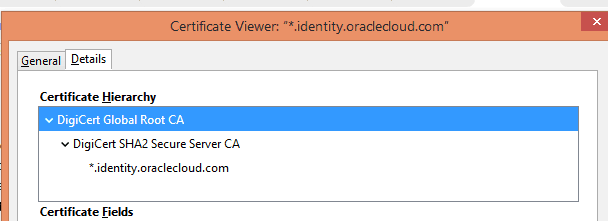
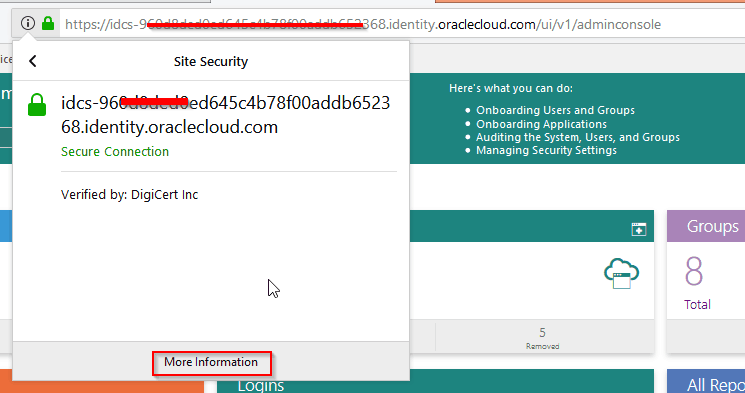
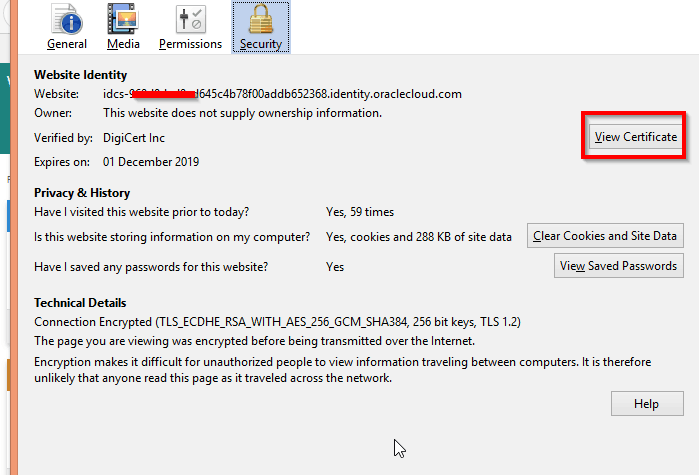
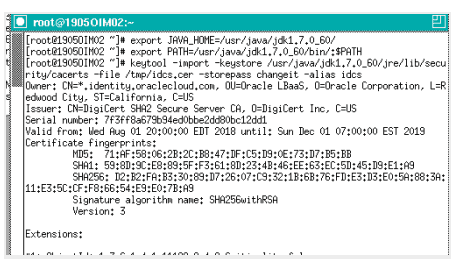
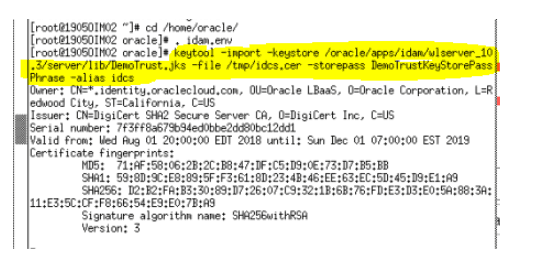
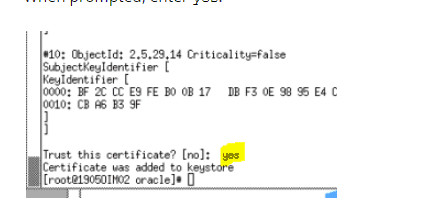
- Check 5: IDCS’s SSL certificate needs to be loaded in OIM’s truststore. How to import IDCS SSL Certificate in OIM TrustStore Click here to check.
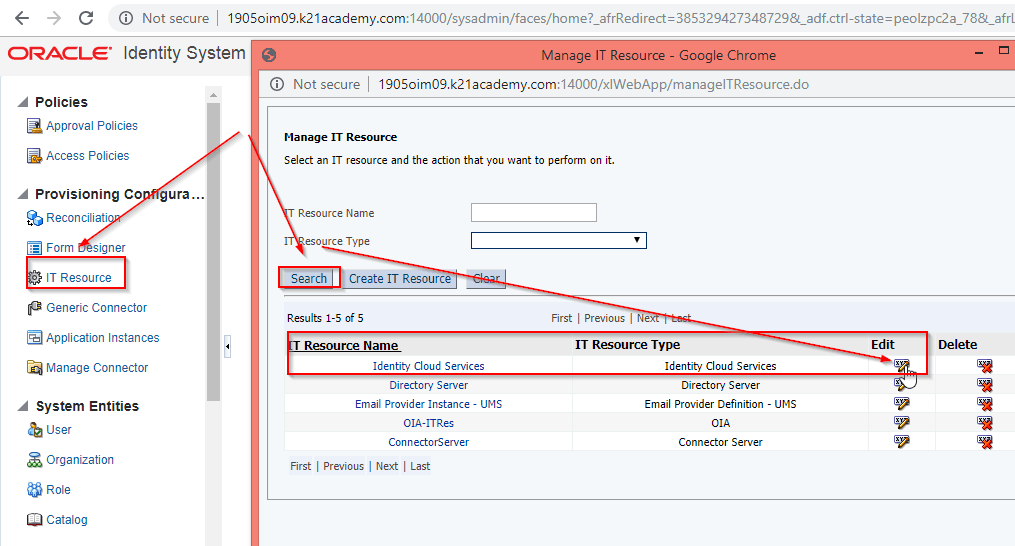
IDCS IT resources in OIM Screen: To Configure IDCS IT Resource parameters in OIM you use the below configuration details. For more details on Configuring the Identity Cloud Service Connector Click here.
Client application in IDCS: Make sure you use the below configuration details when you Create an Application in IDCS. For more details on Register to OIM Application in IDCS Click here
Testing:
We could successfully run the Scheduled jobs in OIM/OIG.
This post is from our Oracle Identity Cloud Service (IDCS) training in which we have covered everything one should know about Oracle Identity Cloud Service like Architecture, Users & Groups Application, Branding, Auditing & Reports, Rest APIs, Adaptive security and much more.
Interested? Register for Free Master Class on Cloud Security Using Oracle IDCS: Career Path & What to Learn?
Related Posts
- Cloud Security With Oracle Identity Cloud Service (IDCS) Click here
- Oracle Identity Cloud Service (IDCS): Step By Step Lab Activity Guide for Beginners Click here
- Oracle Identity Cloud Service (IDCS) Overview & Concepts Click here
- Cloud Security Using Identity Cloud Service Click here
- Oracle Identity Cloud Service: Configuring Multi-Factor Authentication (MFA) Click here
- High-level Steps to Protecting an On-premises Application with IDCS by Using WebGate Click Here
References
- Oracle Identity Cloud Service: Integrating with Oracle Identity Manager (OIM)
- IDCS Group Lookup Reconciliation job fails with: org.identityconnectors.framework.common.exceptions.InvalidCredentialException: HTTP 401 Error : User not authorized to execute service ( Doc ID 2484895.1 )
Register for Free Master Class on Cloud Security Using Oracle IDCS: Career Path & What to Learn?
Next Task for You
Download our FREE Guide i.e., 7 Docs Must Read to Become Expert in Cloud Security With Oracle Identity Cloud Service (IDCS).
Click on the image below to Download the Guide:
The post OIM/OIG – IDCS Connector Integration : [Troubleshooting] InvalidCredentialException: HTTP 401 Error : User not authorized to execute service appeared first on Oracle Trainings.















































 This completes the configuration of the LinkedIn connector.
This completes the configuration of the LinkedIn connector.









 Keys Point About RAC In Cloud (OCI)
Keys Point About RAC In Cloud (OCI)








 in the top left corner of the My Services Console Dashboard. Then Click
in the top left corner of the My Services Console Dashboard. Then Click 







































