This blog post gives a walkthrough of the Step-By-Step Activity Guides that you must perform to learn the AZ-500 Microsoft Azure Security Technologies Training course and clear the Azure Security Engineer Associate.
The AZ-500 Microsoft Azure Security Technologies Training focuses on those individuals who want to implement and manage security controls and threat protection, who can manage the identity and access aspect, and other security aspects in a cloud and hybrid environment as a part of an end-to-end infrastructure.
This post will help you with your self-learning and clearing your certification. There are 15 Hands-on Labs included in this course by Microsoft.
- Register For A Free Azure Cloud Account
- Role-Based Access Control
- Azure Policy
- Resource Manager Locks
- MFA, Conditional Access and AAD Identity Protection
- Azure AD Privileged Identity Management
- Implement Directory Synchronization
- Network Security Groups and Application Security Groups
- Azure Firewall
- Configuring and Securing ACR and AKS
- Create an Azure Bastion Host
- How to Encrypt A Virtual Machine
- Update Management in Azure
- Key Vault (Implementing Secure Data by setting up Always Encrypted)
- Securing Azure SQL Database
- Service Endpoints and Securing Storage
- Azure Monitor
- Azure Security Center
- Azure Sentinel
Activity Guides:
1) Register For A Free Azure Cloud Account
Creating an Azure free account is one way to access Azure services. When you start using Azure with a free account, you get USD2001 credit to spend in the first 30 days after you sign up. In addition, you get free monthly amounts of two groups of services: popular services, which are free for 12 months, and more than 25 other services that are free always.
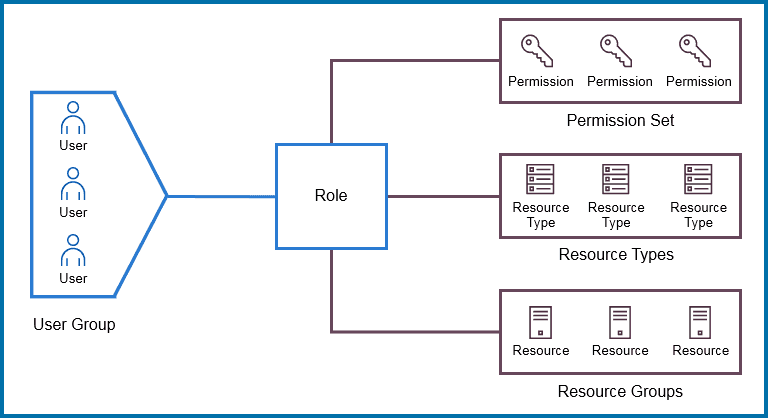
2) Role-Based Access Control
Here, you need to create a user group and users and provide role-based access to specific users/user groups. Role-based access control is an approach that’s used for restricting access to users and applications on the system/network. This approach is widely used in today’s market for security and access control.
3) Azure Policy
Azure Policy restricts resource creation in a specific location and it can also be used in more depth also.
Here, you need to create an Azure Policy to restrict resource creation in specific regions and test your policy, also.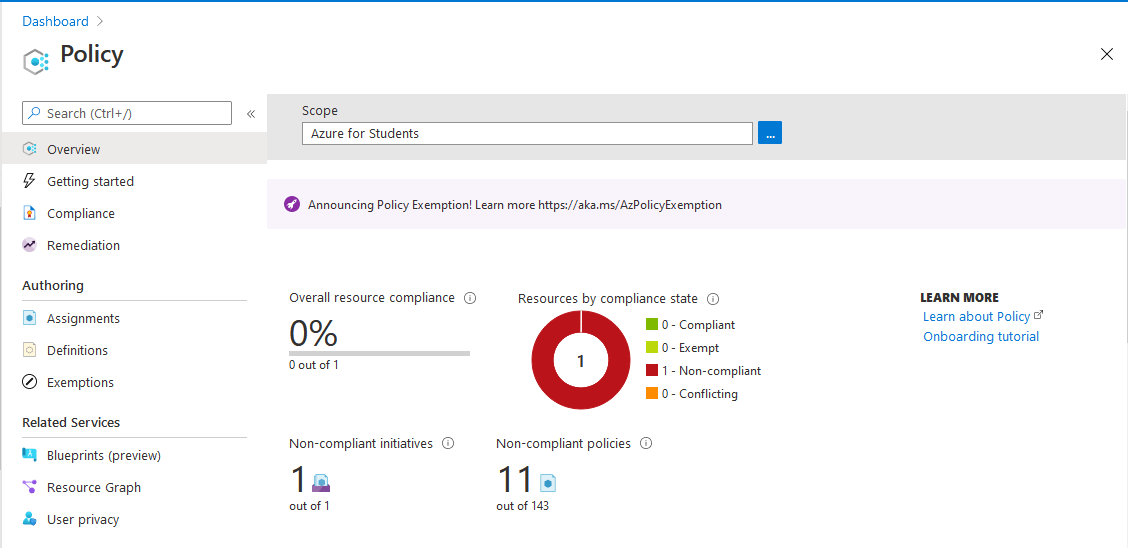
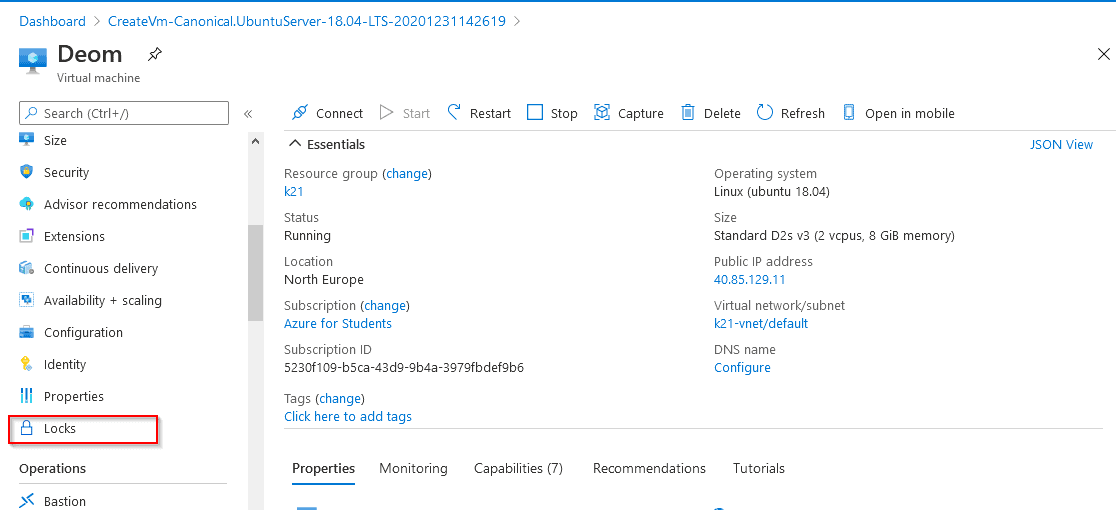
4) Resource Manager Locks
Resource Manager Locks are used by admins to lock Azure Resources to prevent accidental changes or deletion of the resources by users while testing or doing some work.
Here, you need to create locks on specific resource groups to avoid accidental changes or deletion.
Also Read: How to create a chatbot in Microsoft Azure ( Azure Chatbot )
5) MFA, Conditional Access, and AAD Identity Protection
Multi-Factor Authentication is one of the very crucial steps for any organization that wants to implement a higher level of security. In Azure, Conditional Access and Azure Active Directory Identity Protection are used for the purpose of MFA.
Here, you need to create a VM and then implement Multi-Factor Authentication that will use Azure Active Directory Services for Authentication.

Go through this Microsoft Azure Fundamentals Blog to get a clear understanding of Exam AZ-900: Microsoft Azure Fundamentals
6) Azure AD Privileged Identity Management
Azure AD Privileged Identity Management service allows Admins to manage and control user access to high-level resources of the organization.
In this Activity Guide, you’ll create resources in Azure and then implement access restrictions on users for accessing the resources.

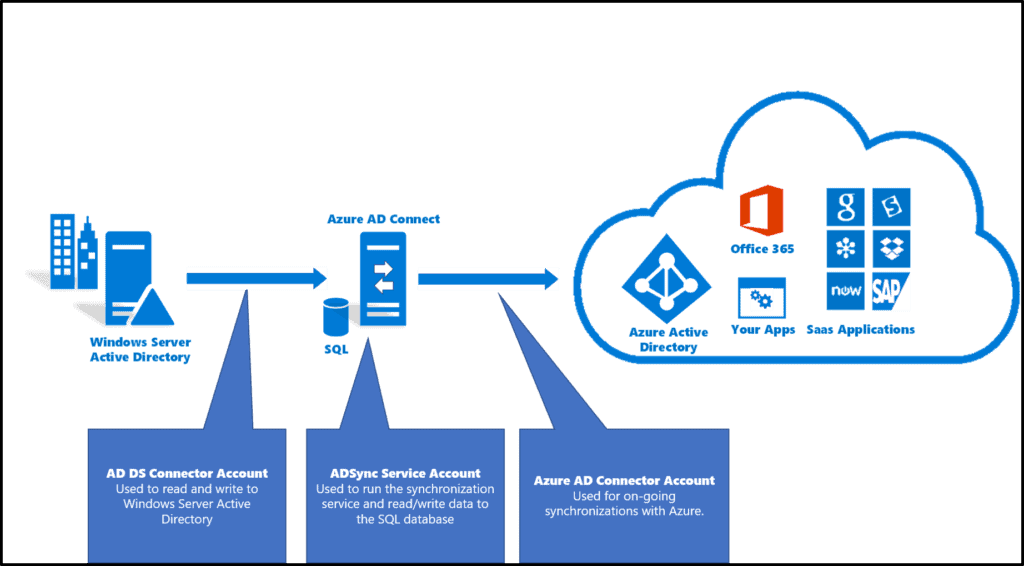
7) Implement Directory Synchronization
Azure Directory Synchronization is a tool that allows users to Manage Identities of Azure Active Directory and also to manage all the updates of user accounts, groups, and contacts that are synced to the Azure Active Directory Tenant.
In this Activity Guide, you will work with Active Directory Domain Services where you will be creating an Azure Domain Forest and Creating an Azure Active Directory Tenant and synching them.
Also check: How to create a Load Balancer in Azure using the Azure Portal.
8) Network Security Groups and Application Security Groups
Network Security Groups are used in an organization to filter the network traffic flow of an Azure Virtual Network. NSGs have security rules in them that can be used to restrict inbound/outbound traffic from different kinds of Azure Services.
In this Activity Guide, you’ll have to configure the Network Security Group rule for a group of Servers to perform to RDP. 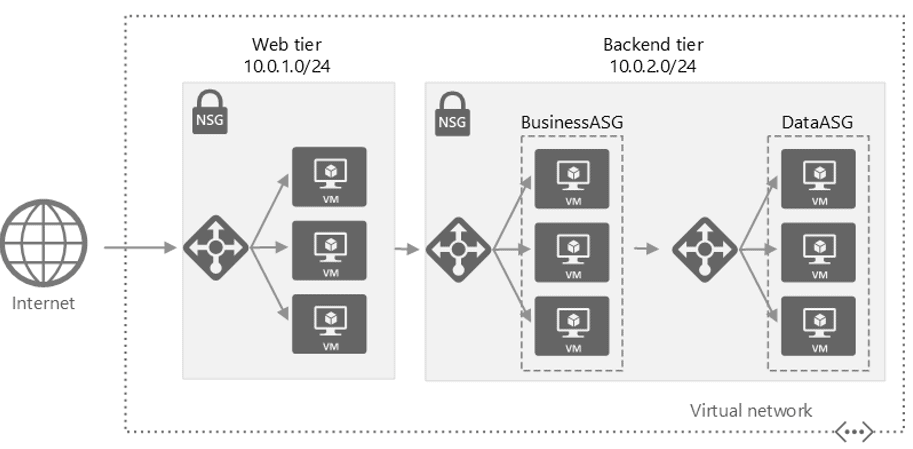
9) Azure Firewall
Azure Firewall is a cloud-based network security service in Azure. Azure Firewall protects our Virtual Network Resources and this is a built-in service.
Here, you’ll be Configuring Azure Firewall to control inbound and outbound network access of your organization.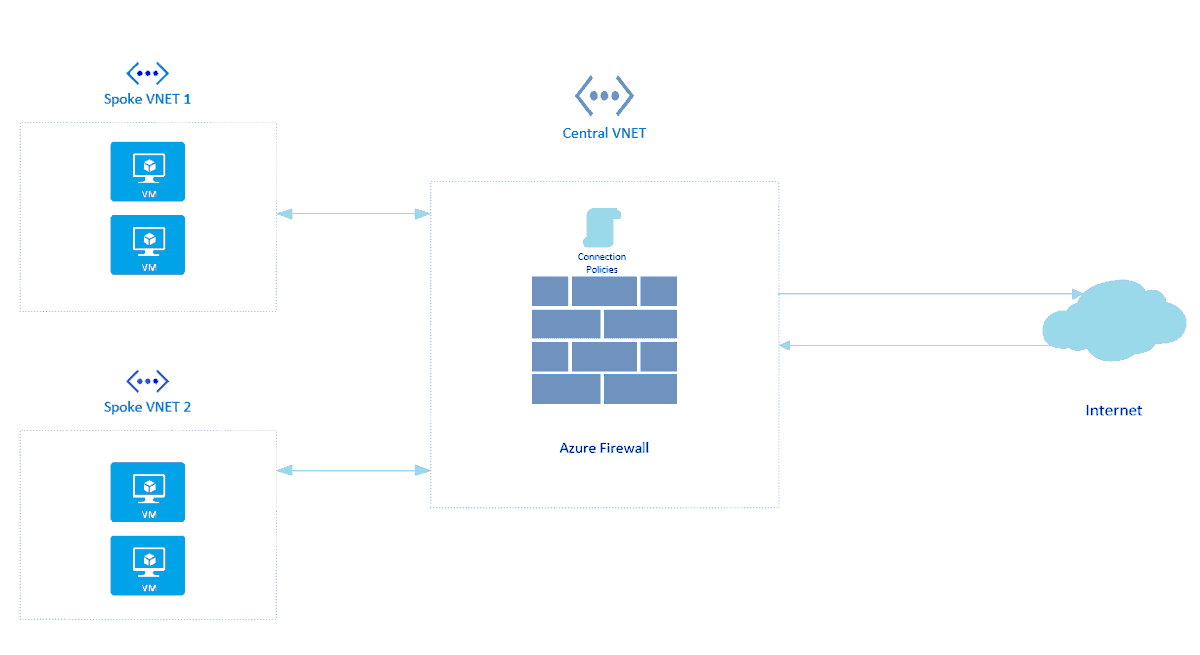
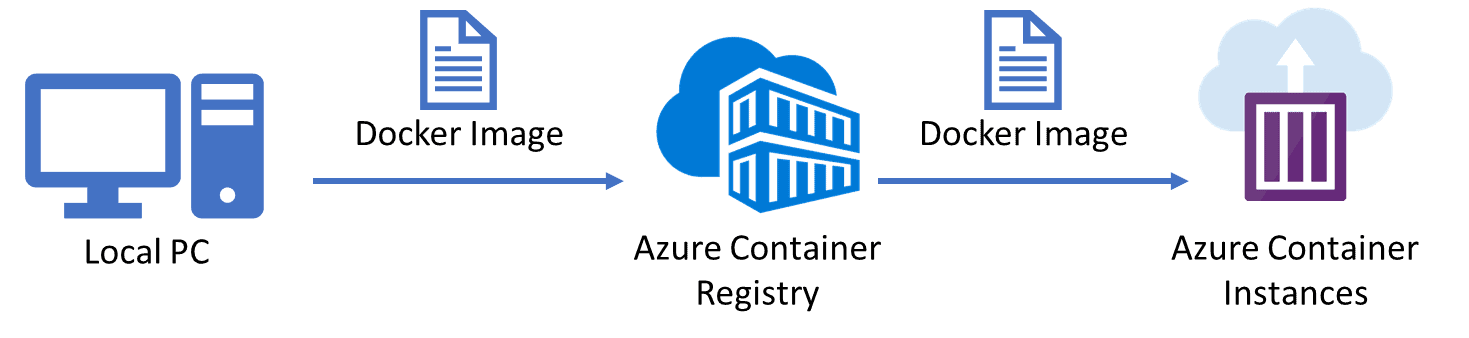
10) Configuring and Securing ACR and AKS
Azure Container Registry (ACR) is a managed, private Docker registry service based on the open-source Docker Registry 2.0. Create and maintain Azure container registries to store and manage your private Docker container images and related artifacts.
There are security benefits to working with ACR. Firstly, it provides signed container images, so your Kubernetes cluster can verify that the code it’s running is the code you pushed to your registry from your build system
You can log in to a registry using the Azure CLI or the standard docker login command. Azure Container Registry transfers container images over HTTPS and supports TLS to secure client connections.
Azure Kubernetes Service (AKS) is a fully-managed service that allows you to run Kubernetes in Azure without having to manage your own Kubernetes clusters. Azure manages all the complex parts of running Kubernetes, and you can focus on your containers.
For improved security and management, AKS lets you integrate with Azure AD to use Kubernetes role-based access control (Kubernetes RBAC).
11) Key Vault (Implementing Secure Data by setting up Always Encrypted)
Azure Key Vault as the name suggests is a service provided by Azure Cloud to store all the keys, passwords, and certificates.
Always Encrypted is a data encryption technology that ensures that sensitive data remains always encrypted and never shows as plaintext in a database, whether it’s at rest, moving between client and server or it’s in use.
12) Securing Azure SQL Database
In this Activity Guide, we will help you to Secure an Azure SQL Database by creating rules in Azure Firewall to prevent various attacks such as SQL Injection and Data Exfiltration.
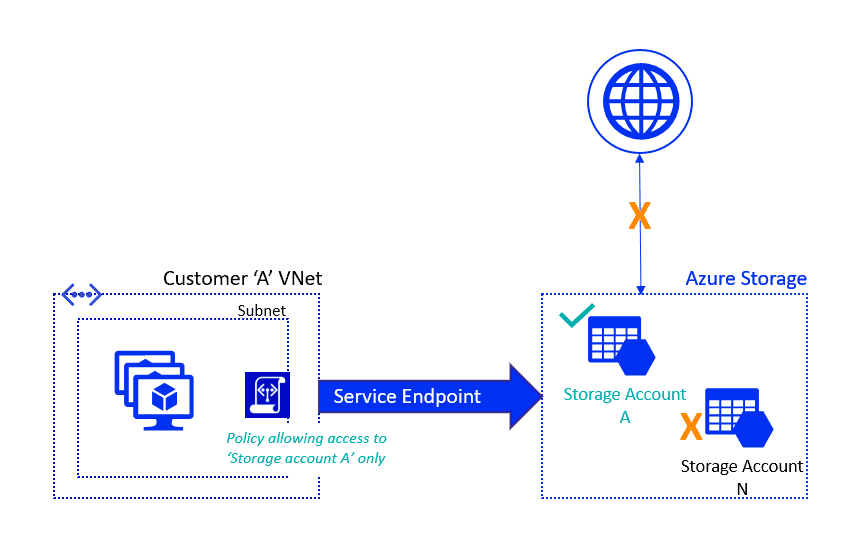
13) Service Endpoints and Securing Storage
The Virtual Network service endpoint provides a secure and direct connection to Azure Services. Service Endpoint removes the need for a Public IP address to access an endpoint of an Azure service and this is done by enabling a Private IP address in the Vnet by using Service Endpoint.
14) Azure Monitor
Azure Monitor is a monitoring service provided by Azure. Using Azure Monitor helps to maximize the performance and availability of businesses. The Azure Monitor acts on the telemetry of the Cloud and On-Premises Environments and provides the optimum configurations for the resources.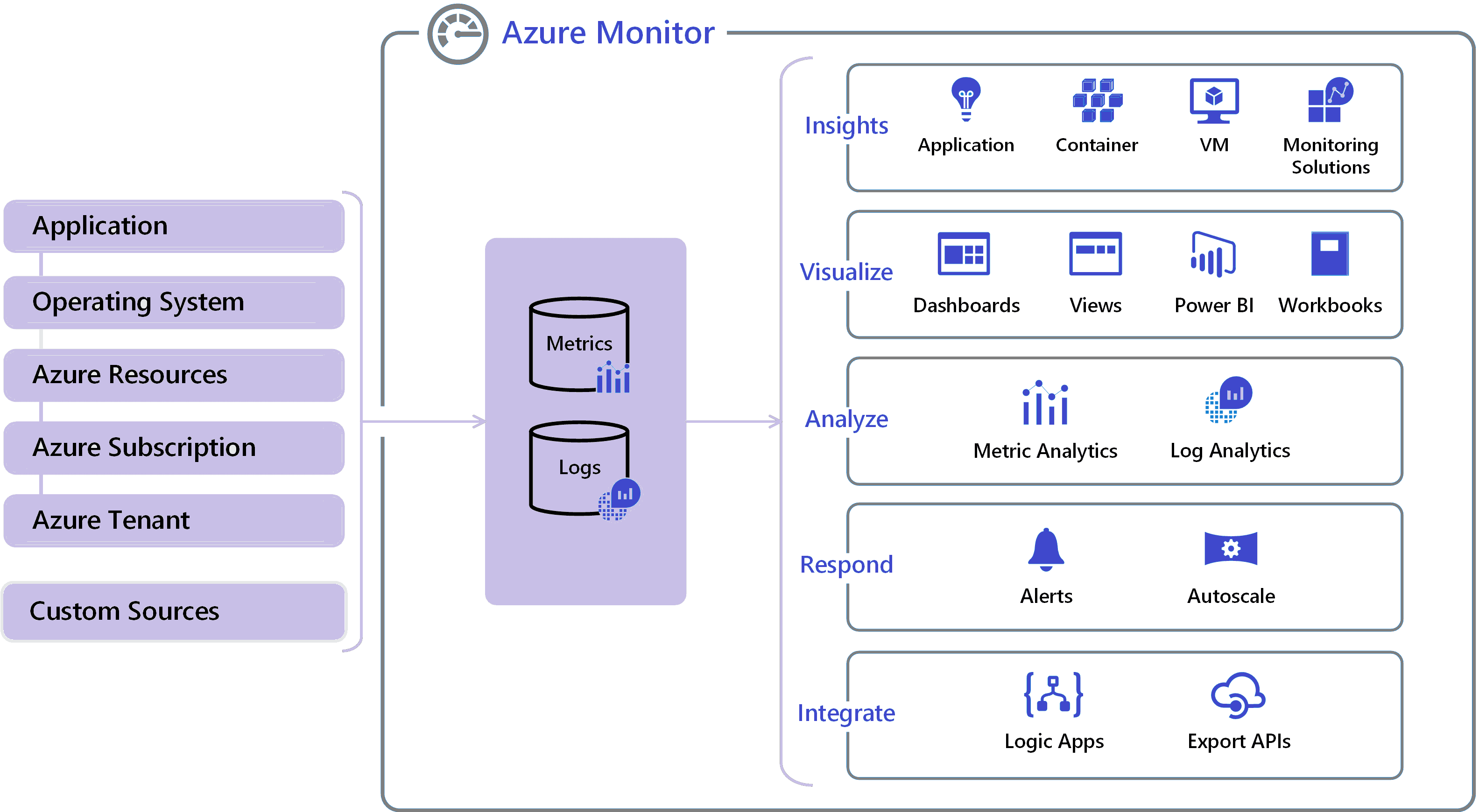
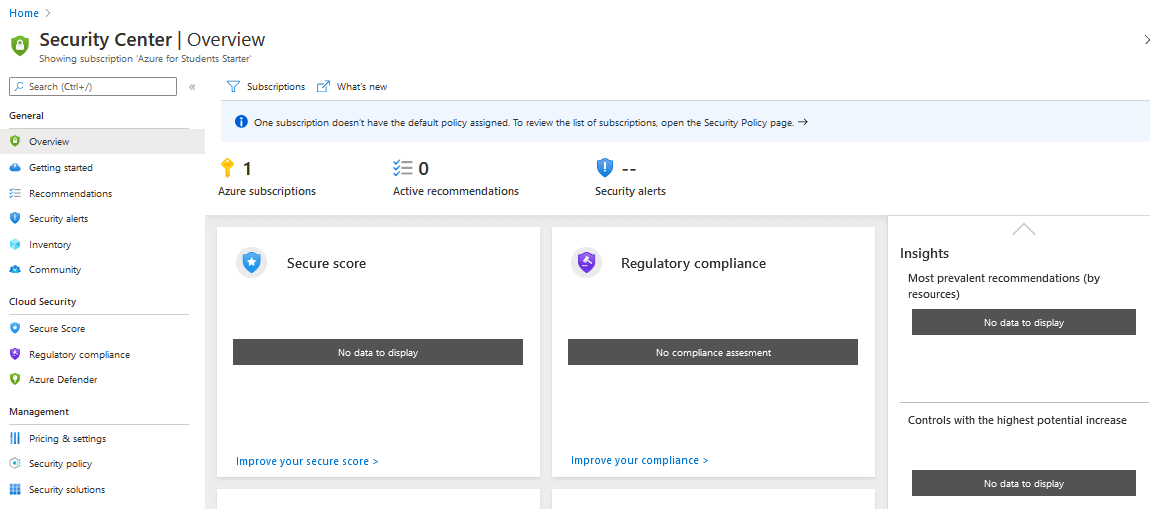
15) Azure Security Center
Azure Security Center is an infrastructure tool provided by Azure Cloud for security management and threat protection. This tool provides security to Cloud Resources and On-premises Resources as well.
16) Azure Sentinel
Azure Sentinel is a very advanced service of Azure. It is a scalable, cloud-native, security information event management, and security orchestration automated response solution.
In this Activity Guide, you’ll have to collect data from the Azure Activity and Security Center. And also you have to add built-in and custom alerts.

Next Task For You
Once you have practised all the listed hands-on for Microsoft Azure Security Technologies, you should appear for the Microsoft Azure Security Technologies certification. Click here to know all about the Microsoft Azure AZ-500 examination.
Begin your journey towards becoming a Microsoft Azure Security Technologies Engineer and earn a lot more in 2023 by joining our Free Class.
Click on the below image to Register for the FREE CLASS Now!
The post Microsoft Azure Security Cloud AZ-500 Step by Step Hands-on Labs appeared first on Cloud Training Program.