
Containers and Kubernetes as technology is dominating the job market. In order to get a higher-paying Job, one should be familiar with Kubernetes from DevOps, while working in IT.
To be production-ready, Kubernetes must meet a number of requirements. It must also meet organizational requirements for logging and monitoring, be secure, scalable, highly available, and reliable in addition to having built-in disaster recovery capabilities. Kubernetes must be able to support the requirements of governance and compliance standards in an enterprise setting.
In this blog post, we are going to discuss the top 10 actions you should take in a production K8s environment!
Implement liveness and readiness probes
Use readiness and liveness probes to make sure your containerized app is operating as intended. Make sure a pod’s container is powered on, running, and performing its necessary functions.
Health checks, also known as probes, are how Kubernetes are monitored for their “health” to determine whether they are functioning properly and receiving traffic. It is used to check whether active, responsive instances of an application are running.

LivenessProbe for Kubernetes Probe for Kubernetes readiness You are correct; Kubernetes does detect failures and restart pods. But in some circumstances, even K8s require assistance, such as when:
- Although the process isn’t completely dead, it enters a deadlock and stops functioning.
- Technically, the application is not stuck. It cannot, however, handle any requests.
This is resolved by Kubernetes using probes. But first, let me describe the Pods’ lifecycle so that we can get to know them.
 Know more about liveness and readiness probes here.
Know more about liveness and readiness probes here.
Namespaces
Namespaces offer a way to partition Kubernetes clusters into virtual sub-clusters when numerous teams or projects use the same cluster. Any number of namespaces can be supported by a cluster, and even though they are logically isolated from one another, each one can still communicate with the others. It is not possible to nest namespaces inside of one another.
The default namespace or a namespace that the cluster operator specifies can contain any resource in Kubernetes. Outside of the namespace, only nodes and persistent storage volumes exist; each namespace in the cluster has continuous access to these basic resources.
Use namespaces to implement a fundamental level of separation. This is not a piece specifically designed for “security segregation,” nor should it be viewed as such, but it’s a good beginning.
 Know more about namespaces here.
Know more about namespaces here.
Scalability
In production, it’s very crucial to set up your scaling correctly for both Pods and the cluster (control plane and worker nodes) and ensure that the resources on the cluster for Pods are available.
Three tools are already included in Kubernetes to support scalability. To fine-tune scaling behavior, you should employ all three in production.
- Cluster Autoscaler: The Cluster Autoscaler increases or decreases the cluster size by adding or removing nodes.
- HPA: A ReplicaSet or deployment’s pods are scaled using pre-defined metrics by the horizontal pod autoscaler.
- Vertical Autoscaler: Utilization metrics are used by the vertical autoscaler to specify resource limits and requests for each individual container.
You can guarantee a scalable Kubernetes environment in production when you use all three autoscaling processes.
 Know more about scaling of pods here.
Know more about scaling of pods here.
Cluster Monitoring and Logging
Kubernetes can typically scale to hundreds of pods when used in production. Downtime can result in serious, irreversible errors that can affect customer and business satisfaction if monitoring and recording are not effective.
Monitoring gives your Kubernetes infrastructure visibility and precise metrics. From individual containers or virtual machines to servers, networking performance, and storage usage, it can provide metrics on the use and performance of resources from private clouds or public cloud providers.
You can implement centralised log management using either proprietary or open source tools, such as the EFK stack, which consists of Fluentd, FluentBit, Elasticsearch, and Kibana.
In addition to being watched over constantly, Kubernetes ought to offer a role-based dashboard with live alerts for important performance indicators like performance, capacity management, and production problems.
Ensure that you implement both monitoring AND observability practices.
Networking
Understanding networking deeply, at least at a CCNA level. Networking makes up 60-70% of Kubernetes.
Kubernetes networking enables the communication between Kubernetes components like pods, containers, API servers, etc. Because it is built on a flat network structure, the Kubernetes platform differs from other networking platforms in that it does not require mapping host ports to container ports.

The Kubernetes platform offers a method for managing distributed systems by allowing applications to share machines without having to dynamically assign ports. The system is greatly complicated by the dynamic port allocation.
 Know everything about networking here.
Know everything about networking here.
Role Based Access Control (RBAC)
Role-Based Access Control is referred to as RBAC. It’s a method for restricting access to users and programs on the system or network. Role-based access control, or RBAC, is a security approach that limits access to valuable resources based on the role that the user currently occupies.
RBAC is a technique for controlling access to a computer or network resources based on the roles of specific users within an organization. In this context, access refers to a private user’s capacity to carry out a particular task, such as reading, creating, or altering a file.

Proper authentication and authorization with RBAC and/or another OIDC solution are needed from Day 1. Why access control is usually of interest to us We obviously have a lot of users in our groups because they are able to access our Kubernetes cluster. They must all feel some degree of protection from one another. There may be instances where one of our team members unintentionally obstructs the work of another team member.
 Know everything about RBAC here
Know everything about RBAC here
Service Mesh
A network-based infrastructure layer called a service mesh controls service-to-service communication. This allows various parts of a program to communicate with one another. Microservices, containers, and cloud-based apps are frequently combined with Service Mesh.
It controls how service requests are delivered within an application. Common components of a Service Mesh include service discovery, load balancing, encryption, and failure recovery. It is also common practice to use software controlled by APIs rather than hardware to achieve high availability. By making service-to-service communication more effective, dependable, and secure, service meshes may enhance this communication.

 Know everything about Service Mesh here
Know everything about Service Mesh here
Scan container images
Scanning container images with a tool that allows you to see a remediation process vs just scanning and forgetting about it. The process of scanning your Docker image for known security flaws in its packages is known as scanning. Before submitting the image to a registry or using it as a container, you can use this to identify vulnerabilities in container images and fix them. We are given a scan command by Docker. There are also numerous other open-source tools available in addition to those. Let’s examine how to use the Trivy tool to scan the Docker Images.
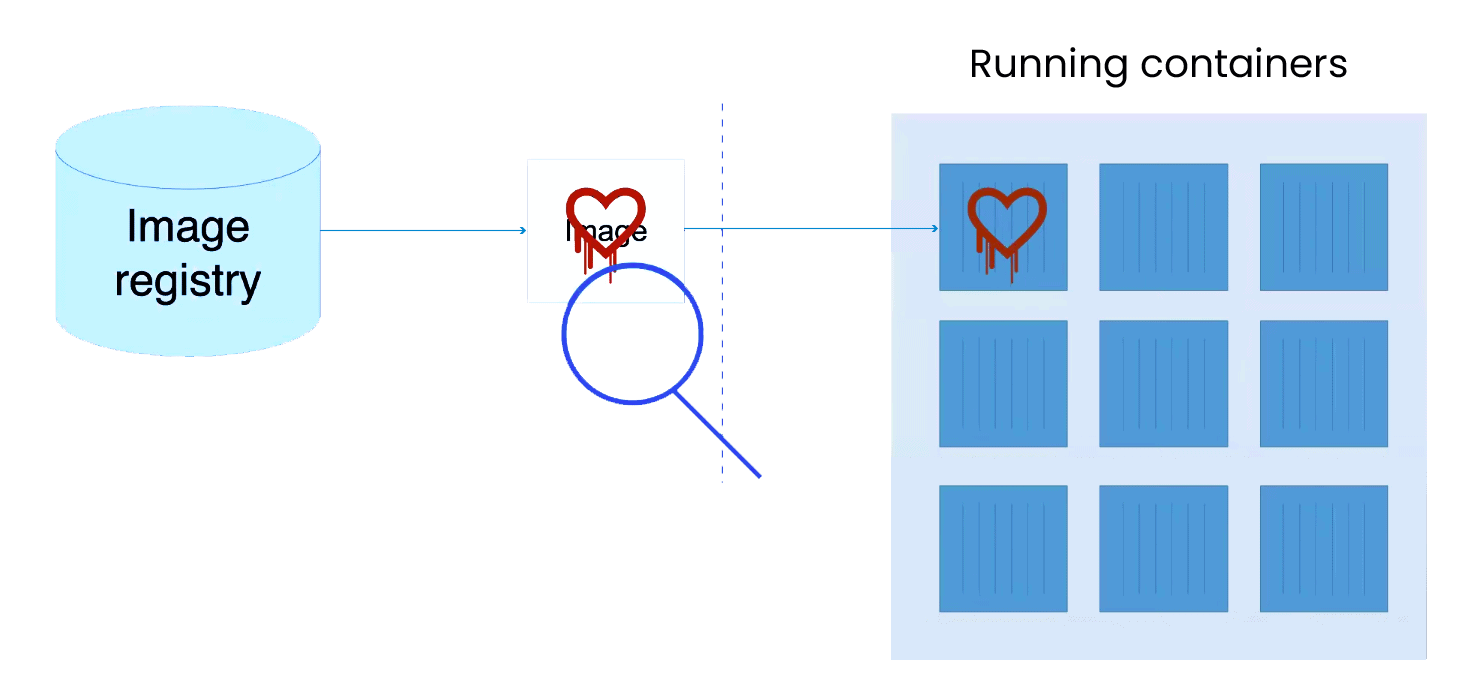
The tools recognize the package and version in the image and also perform cross-references with the database of vulnerabilities. Since there are numerous Linux image distros, identifying these vulnerabilities in detail becomes a monumental task. Not to mention any security updates that the vendor may backport.
 To learn more about scanning images, click here
To learn more about scanning images, click here
Kubernetes as a Service
The most well-liked container orchestrator in the world, K8s, can be used as a managed service thanks to Kubernetes as a Service (KaaS). The public cloud is where KaaS services are frequently offered, but some KaaS platforms can also be set up on-site.
A KaaS platform’s primary functions are to deploy, oversee, and maintaining Kubernetes clusters. Self-service deployment, Kubernetes upgrades, scalability, and multi-cloud portability are some of the main features of Kubernetes as a Service.
The most well-known Kubernetes as a Service platform are listed below.
- Kubernetes on Amazon – Amazon EKS (Elastic Kubernetes Service)
- Kubernetes on Azure – Azure Kubernetes Service (AKS)
- Kubernetes on Google – Google Kubernetes Engine (GKE)
Kubernetes for Business
Monolithic applications might be comfortable and familiar, but they won’t grow with your company. You will eventually need to switch to a platform that is adaptable enough to manage the increased load and computing requirements as your business expands. Adopting Kubernetes for your company is the answer, and it has the added benefit of making your applications adaptable to any environment.
A 2020 IBM Market Development & Insights study found that 45% of IT executives and 59% of developers thought containerization was essential for third-party applications and internal operations. In the same study, Kubernetes and other container orchestration platforms were used to manage containerized environments by 70% of developers and developer executives. According to SlashData’s survey of backend developers in 2021, 31% of them said Kubernetes was their preferred platform—a 4% increase from the previous year.
These numbers appear to be large. According to reports, 21% of developers who were asked about back-end development were only vaguely familiar with Kubernetes’ purpose, and 11% hadn’t even heard of it.
The orchestration of containers using Kubernetes is a great way to secure your company’s future. It increases the portability, scalability, and economy of your applications. Additionally, K8s provides a wide range of tools to streamline resource management, improve teamwork, and accelerate deployments.
However, you should transition to scalable, loosely-coupled software architecture first before implementing Kubernetes. To fully reap the rewards of K8s, you’ll also need a team with DevOps expertise.
Related/References
- Visit our YouTube channel “K21Academy”
- Certified Kubernetes Administrator (CKA) Certification Exam
- (CKA) Certification: Step By Step Activity Guides/Hands-On Lab Exercise & Learning Path
- Certified Kubernetes Application Developer (CKAD) Certification Exam
- (CKAD) Certification: Step By Step Activity Guides/Hands-On Lab Exercise & Learning Path
- Create AKS Cluster: A Complete Step-by-Step Guide
- Container (Docker) vs Virtual Machines (VM): What Is The Difference?
- How To Setup A Three Node Kubernetes Cluster For CKA: Step By Step
Join FREE Masterclass
To know about what is the Roles and Responsibilities of Kubernetes administrator, why you should learn Docker and Kubernetes, Job opportunities for Kubernetes administrator in the market, and what to study Including Hands-On labs you must perform to clear Certified Kubernetes Administrator (CKA) certification exam by registering for our FREE Masterclass.
The post Kubernetes in Production: Top 10 actions you should take appeared first on Cloud Training Program.

